Cloud and Cybersecurity Makeover: Apply Now
We’re thrilled to announce a game-changing opportunity: $100,000 in resources to help you plan, execute, and thrive in the cloud.
{% video_player "embed_player"...
We’re thrilled to announce a game-changing opportunity: $100,000 in resources to help you plan, execute, and thrive in the cloud.
{% video_player "embed_player"...
Danvers, MA — Aug. 12, 2025 — NetCov is pleased to announce the elevation of Jen Anthony and Andrea DiGiacomo to two new C-level roles, designed to strengthen how the company...
.png)
At this year’s Southeastern Association of Goodwill’s (SEA) Conference, NetCov proudly joined more than 100 leaders representing 26 Goodwill organizations—all united by a shared...

Network Coverage, an MSP based in Danvers, MA, supports clients across regulated...

Network Coverage has a trio of exciting announcements to share, all of which mark a major step forward for the company.
...

Network Coverage first started working with the fast-growing construction management company in...

A construction management firm was blindsided by a ransomware attack that infected their workstations and...

A recent cybersecurity threat has been identified involving Microsoft Teams. According to a recent report, cybercriminals are exploiting Teams to conduct vishing (voice phishing)...

NetCov receives the MSP Rising Star award at the Golden Datto Awards. Pictured (left to right): Dan Tomaszewski (Kaseya), Chris Sachse (CEO, NetCov), and Eric Tomah (CTO, NetCov).

NetCov has been named Arctic Wolf’s MSP East Partner of the Year for 2025 —a distinction that celebrates top-performing managed service providers driving real cybersecurity...

Recent geopolitical developments have increased the likelihood of elevated cyber activity targeting U.S. organizations and infrastructure. Government agencies and cybersecurity...

Danvers, MA — Feb. 12, 2026 — NetCov has been named to the CRN® 2026 MSP 500 list in the Elite 150 category, recognizing top-performing managed service providers delivering...
.png)
We’re proud to announce that NetCov has been selected as a finalist in three prestigious categories at the 2025 MSP Titans of the Industry Awards — one of the most respected award...
%20(1).png)
Danvers, Mass. — Dec. 7, 2025 — NetCov is proud to announce that Think|Stack, a NetCov company, was named a finalist for the 2025 AWS Nonprofit Consulting Partner of the Year...

Organizations rarely fail because they lack technology.
They fail because they’ve layered tools faster than they’ve built processes or trained people.
We see it every day:...

Cybersecurity programs can be complex.
But the single highest-impact activity you can run this quarter requires no new software, no procurement, and no long deployment cycle.
It’s...

If leadership doesn’t show that cybersecurity is a priority, no one is going to take it seriously.
When executives engage personally in security initiatives, employees follow...

Most organizations talk about cybersecurity in terms of tools—firewalls, EDR, or AI-driven analytics.
But after three decades of protecting businesses across industries, we’ve...

October might be Cybersecurity Awareness Month, but the truth is that cybersecurity never takes a holiday.
At NetCov, we’ve spent nearly 30 years helping organizations—from...

NetCov receives the MSP Rising Star award at the Golden Datto Awards. Pictured (left to right): Dan Tomaszewski (Kaseya), Chris Sachse (CEO, NetCov), and Eric Tomah (CTO, NetCov).
.png)
At this year’s Southeastern Association of Goodwill’s (SEA) Conference, NetCov proudly joined more than 100 leaders representing 26 Goodwill organizations—all united by a shared...

Danvers, MA — Aug. 12, 2025 — NetCov is pleased to announce the elevation of Jen Anthony and Andrea DiGiacomo to two new C-level roles, designed to strengthen how the company...

NetCov's Bridget Wilson (Senior VP of Governance, Risk & Compliance) connected with Egnyte's Neil Jones (Director of Cybersecurity Evangelism) for their latest webinar, guiding...

In financial services, staying secure isn’t just about deploying more tools. It’s about combining technology with strategic foresight.
I recently joined Neil Jones at Egnyte’s...

As part of our ongoing commitment to keeping you informed of relevant cybersecurity news and events, we wanted to flag a situation that occurred over the holiday weekend.
One of...



NetCov has been named Arctic Wolf’s MSP East Partner of the Year for 2025 —a distinction that celebrates top-performing managed service providers driving real cybersecurity...

A construction management firm was blindsided by a ransomware attack that infected their workstations and...

A Massachusetts-based event rental and services company was experiencing rapid growth, acquiring new...

An enterprise-level construction company based in the Southeast U.S. was...

As the 4th largest general contractor in Massachusetts, Commodore...

NexRep’s BYOD contact center model was ahead of the curve, but as demand exploded—especially from healthcare clients—securing...

A global safety equipment manufacturer was struggling to manage file access across a growing network of offices and distribution...

Network Coverage, an MSP based in Danvers, MA, supports clients across regulated...

We’re thrilled to announce a game-changing opportunity: $100,000 in resources to help you plan, execute, and thrive in the cloud.
{% video_player "embed_player"...
Network Coverage first started working with the fast-growing construction management company in...

A recent cybersecurity threat has been identified involving Microsoft Teams. According to a recent report, cybercriminals are exploiting Teams to conduct vishing (voice phishing)...

Dec. 16 is a seminal date in the intricate world of Governance Risk and Compliance (GRC).
The U.S. Department of Defense’s Cybersecurity Maturity Model Certification Program...

Artificial Intelligence is enhancing productivity and driving innovation. Has your organization started to take advantage yet? While there are numerous benefits, companies...

Cybersecurity Maturity Model Certification, or CMMC, compliance is necessary for all businesses, big or small, engaging with the Department of Defense (DoD). However, the actual...

CMMC compliance is not a one-and-done job, but rather an ongoing process. Working with the right partner for your cybersecurity needs can make all the difference, as even minor...

Network Coverage, a best-in-class technology solutions provider, is excited to welcome James Beaman as the organization’s new Chief Financial Officer. Beaman comes to Network...

Network Coverage is proud to announce that the company placed 55th on Channel Futures MSP 501 list for 2024, ranking among the top managed service providers across the globe.
...

Network Coverage is excited to share that we finished as a 2024 XCellence Award finalist in multiple categories at the Midsize Enterprise Summit (MES) Spring conference, hosted by...

Network Coverage has a trio of exciting announcements to share, all of which mark a major step forward for the company.
...
As cyber threats evolve and become more sophisticated, the demand for robust privacy and security measures has reached an all-time high. Industries, corporations, and individual...
The stakes for application security have never been higher. With cyber threats constantly evolving and becoming more sophisticated, the need for robust defense mechanisms is...

The average ransom demanded by cybercriminals...

We live in a world where digital data is increasingly valuable and vulnerable to malicious attacks. Cybersecurity has become an essential part of our lives but still leaves gaps...

The innovative technology of blockchain is becoming increasingly important in businesses worldwide. Small and large businesses are also looking to capitalize on this...

Phishing remains the most popular cybercrime suffered by U.S. businesses and individuals. The criminals typically use social engineering to trick victims

Digital privacy is becoming a growing concern and people are waking up to how their personal data is being exploited by unrelenting marketing companies and cyber criminals. In...
Chain businesses are a significant part of our world now. This includes businesses with multiple public locations, like McDonald’s and Target, as well as those with fewer public...

When it comes to IT, there’s a day and an age for everything. Remember when we thought it would never get better than dial-up internet? How about when we got hard drives with one...

There is no denying that data centers are an integral part of our technology and data-driven future. One of the biggest concerns is the number of greenhouse gases produced from...

There are mini investments that produce healthy returns and create both enormous tax revenue and new jobs. A few of them are as repeatably successful as the modern data center....

IT consultants are technology professionals who help design and execute a strategy for better leveraging technology in your company. This includes using technology to streamline...

The sole act of keeping and maintaining data backups is one of the most important things a business can do. This is true no matter what size a business is or what industry they...

“The war with Russia” hearkens back to the days of the Cold War with the Soviet Union. Back during the 1950s, students in schools all across...

As the threat of cyberattacks grows, protecting sensitive business data is important. For small businesses, the stakes are even higher in some...

In “technology time”, a few months is the difference between bleeding edge and obsolesce — at least that’s the running joke. Truthfully,...

There are lots of things that get lost in life — keys, wallets, top-secret security thumb drives — but aside from that last one, as a business,...

Building a data center is a very involved process. From building materials to air management, there are a lot of physical comments that...

Ask any IT team what the fastest way to a critical system failure is and the answers will vary. “We need protection against...

Over the last decade or so, VoIP phones have almost completely replaced the landlines of old, mainly due to ease of access, vast feature sets, and usually...

During the past three decades, since the advent of the internet, our technological evolution has witnessed dramatic development....

A VPN, Virtual Private Network, is a service added to your internet that lets you access the web privately and safely. It routes your...

Effective IT strategy begins with a deep look into business strategy. Most companies see IT as a necessity for performing operations. However,...

Computer access has evolved a great deal over the years. It used to be that the only manner of operating a computer was to interact with the...

There is no doubt about the massive popularity surrounding software-as-a-service, commonly referred to as SaaS. Estimates state that nearly nine of every ten businesses are using...

Running a successful business is a challenge, no matter the size of the organization. Whether large or small, companies are a complex set of operations and equations. And to make...

You might have heard about “the cloud,” but do you know what it is and how to use it as a business tool? Cloud computing is a great...

This question used to be one of those “40,000 feet above” questions — it was more of a psychological test rather than an...
With Artificial Intelligence making an entrance into our ever-evolving daily life, it is worth taking a bit of time to talk about how...

While some aspects of a company’s IT needs to stay relatively steady such as monitoring systems, data backup, and...
Managing a business is a constant juggling act of being on top of trends, strategies, and analytics – but keeping track of everything...

Managing expenses is core to any size of business. But it tends to be considerably more critical for smaller companies...
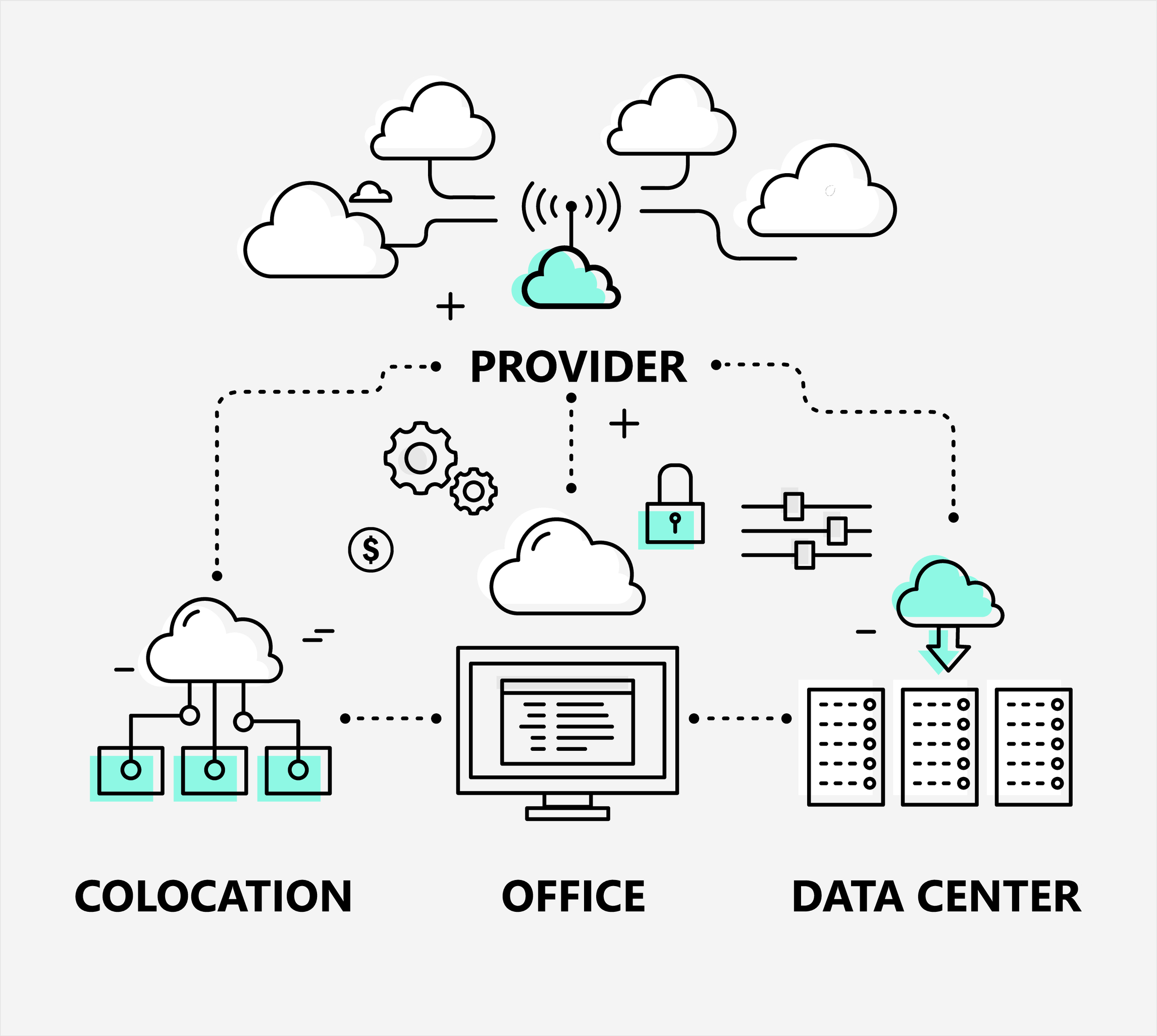
“What type of data center solution is best for me?” This is a common question that many people ask, and for good reason: we need to...

Technology is often filled with buzzwords that create hype for technology companies and confusion for everyone else. The...

It seems there’s not a day that goes by that cybersecurity isn’t being threatened by the likes of criminals and other...

When we think about network capacity, it can be difficult to predict what our businesses will need truly. Anything on our network...
When a business is moving to a new location, getting the IT systems up and running is likely at the top of the priority list....

As you’ve probably witnessed, the last year or two have been different, to put it mildly. With a global pandemic, a rise...

Navigating the modern business world can be difficult, especially without experience in tech. Like it or not, technology is a critical part of...

There is no doubt that the world and businesses are being driven by a new level of technology and data. This includes...

The landscape of technology is continuously evolving, and the realm of cloud-based solutions is no exception. Emerging options for cloud technology...

To understand how to prevent almost anything, it is often critical to first understand some of the causes of the thing we want...

A vast expansion of markets for software solutions entails an ever-diversifying landscape of opportunity. But it can also present...

You most likely have come across the term ‘security patch’ in your computer or other electronic devices that get software updates...

Imagine for a moment that you’re building a new house. Once construction is complete, you notice that your sink leaks. You walk...

Virtualization has been a big part of enterprise computing since the mainframe days of the 60s when computing resources were time-shared by universities and large companies....

Revamping your network for a predominantly remote workforce requires a lot of forethought — at least, more than we may have...

If there’s one concept in the technology sector that’s often misunderstood, it’s the cloud. Once a hot and trendy new...

The bitter but straightforward reality is that individuals, businesses, and industries of all types are vulnerable to data security...
As phishing scams grow less transparent by the day, being on high alert for malicious emails meticulously masked as...

There’s no getting around it – working with tech means dealing with a lot of buzzwords, and it’s hard to figure out which ones will...
Having a good understanding of the ways attacks on firewalls are not adequately secured will help stop your...

It turns out having your head in the clouds isn’t such a bad thing. In fact, it could be the best thing if you own a business...

Every year, the IT Trends Study Research Team provides a SIM IT Trends Study which polls 3,971 members to provide information about top IT trends. One of the sections of this...

Ransomware is one of the most virulent, persistent threats to individuals and enterprises around the globe. Businesses can spend...

As the largest companies across the world continue to outsource a growing number of jobs, businesses of all types and sizes find...

Data integrity and accessibility are critical pieces of strategy and infrastructure for modern business. Every company employee...

More than 1,700 publicly reported data breaches occurred in the first half of 2021, exposing 18.8 billion pieces of information,...

Data loss is one of the biggest risks small- to medium-sized businesses face in their longevity and survival. With 93% of businesses experiencing major data losses going out of...

How many files, programs, and communication records does your law firm use on a daily basis to complete your...

“Cloud computing” is a phrase many of us hear but may not understand. This is because it encompasses several different systems and services, making it...

Every business needs a strong support system to help steer it toward success. Whether you...

Running a business in the modern world is full of constantly evolving and dynamic challenges. It can become overwhelming...

From small businesses to large corporations, cybersecurity remains a top priority. Security protocols are not the exclusive interest...

Businesses and organizations often hire IT consultants to help manage and improve their IT services. An IT consultant works with...

Network security is crucial if you’re running a company that uses computers, software, or technology. In recent times, there...

Organizations and businesses of varying sizes are asking the critical question about whether to move to the cloud or remain on-premises....

Within a vastly expanding digital world, the options for software providers can seem endless. It often feels as though new software companies and...
Your office is full of little things you can do to cut costs. One of the easiest ways to do this is by reducing the amount of...

The market for software solutions has experienced significant growth in recent years. An expanding array of options and...

Data has become a household word and standard industry practice, especially over the past three decades. But humans have a long history of recording data. Early forms included...

Your organization or enterprise has put in a great deal of time and effort to establish your network’s infrastructure. Countless hours...

We are all familiar with media representations of kidnap and ransom. A child of a wealthy or powerful parent is taken from the playground, and then a note...

SaaS, or software as a service, has been a part of the enterprise landscape for decades – but thanks to the rise of cloud computing, SaaS has become a driving force in the way we...

Moving your data and operations to the cloud is often described as a means of improving scalability, reducing infrastructure costs, and making it easier to stay updated. However,...

As the first wave of lockdowns and quarantines sprung up all over the world, millions of people switched off their office computers and transitioned into remote work. This...
The shift to remote work may be one of the biggest challenges faced by IT today! It’s a huge challenge to maintain security...

Firewalls are an essential component of any business network. They act as a filter between the network and any...

If an IT consultant told you that backing up data is one of the most important things for your technical team to do...

If you are a small business considering switching your storage and systems to cloud computing, you may be wondering if it’s the...

Server virtualization is hardly a new technology. The practice became popular half a century ago with companies such as IBM and GE as the...

Deciding whether managed IT services or IT consulting is right for your company depends on the capabilities of your current IT team and the state of your existing technology. IT...
Over 50% of small- to mid-sized businesses experience a cyber-attack at some point. These attacks cost on average $149,000 in...

It can be daunting to consider outsourcing IT services for your company. After all, not only do your operations depend on having reliable systems, but so does your company’s...

Business intelligence (BI) is becoming a more popularly-utilized business tool in companies of all sizes. While the strategy of...

For many financial, healthcare, or government contractors, cybersecurity compliance is complicated and daunting. In addition to federal regulations, companies processing personal...

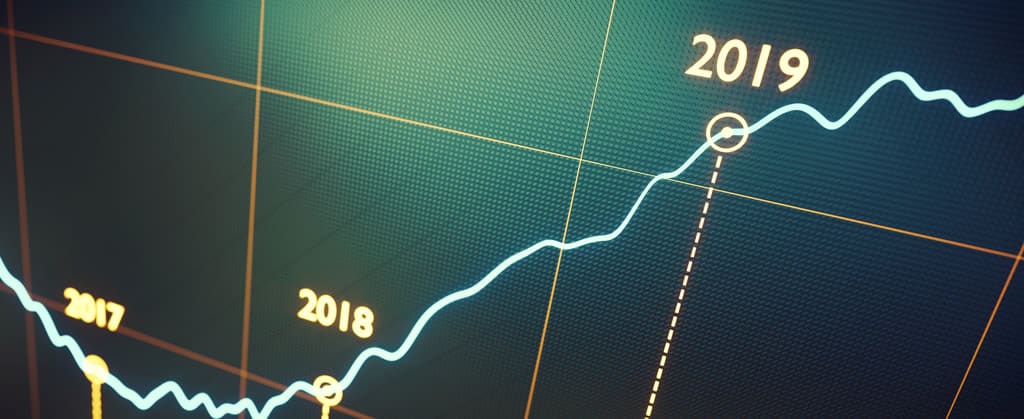
Is your company considering moving some of your infrastructure to the cloud? If so, you’re not alone. According to Gartner Inc., cloud infrastructure spending increased in 2018 by...

Outsourcing IT is sometimes seen as an IT management strategy for small companies to maximize the level of IT service they receive for as little cost as possible. While this is...
Have you seen folks wandering around downtown, staring at their phone like it was a map pointing them to a pot of gold? Or ordering pizza over a Facebook chat conversation with an...

The difference between cloud and hosted services is the location of the servers running the service. “Hosted services” is the...
An increasingly digital world has made it easier than ever to support small and mid-sized businesses. However, this technological convenience comes with a price. Cybersecurity...

With the sensitive data stored and communicated at law firms, it’s no wonder they’re often the target of cybersecurity threats. In the 2017 ABA Legal Technology Survey, it was...

Many people feel they have an understanding of “managed services,” but find they struggle when asked to define it. What, exactly, are “managed services” anyway? What does it mean...

Many sites we visit daily get hacked into by those who try to steal identities or credit card information or both. This causes severe issues with businesses who daily earn our...
Deciding what type of managed services are required for your business takes some time to plan. Simple upkeep or a full suite of services, and anything in between is things that...

How many times have you written that report or taken those amazing once in a lifetime pictures only to have your computer crash and then everything is lost forever? Starting all...

Without sufficient company-wide policies in regard to passwords, your business can be at great risk. The opportunities to take advantage of individuals within a business by...

Hackers are everywhere, and any data they can get is a breach of security. Since security matters every moment of the day, as the network manager, you need to be aware of all the...
Before we talk about the specific scams that you’ll see in your inbox, let’s look at the key factor across all phishing emails: getting you to forward personal information. Any...

Today’s generation is plagued with cybercrimes which are happening day by day. Hackers are discovering new vulnerabilities in networks and...

Continuum Managed Services, makers of the industry-leading IT Management Platform, BDR, and Cyber Security solutions for MSPs, hosted their 4th annual Navigate conference in...

Keeping your company data safe and secured is not an easy job, especially as cyberattack threats get more and more sophisticated every day. But fret not, there are a lot of simple...
Network Coverage was honored with another award this year, this time by one of our newer clients in McCue Corporation. McCue is a manufacturer of “Total Damage Prevention”...
At this year’s Continuum Navigate technology conference, Network Coverage was nominated for two of their partner awards. The first nomination was for Continuum’s Revenue Rockstar...

As we say goodbye to summer and welcome in fall, we say hello to another update to Apple’s...
For some NBA fans, the Milwaukee Bucks have long been a laughingstock on the court. However, their most recent loss is no laughing matter. According to Yahoo! Sports, last month a...
Although WordPress is more secure than it used to be, outdated installations can be a potential threat to your website and the data that is hosted on the servers. In an attempt to...
A simple Google search of “ransomware” returns just over 9 million results. So, too, does a search for “Three Mile Island,” the location of the late-70’s Pennsylvania nuclear...